Using Crypto Investigation to Spot Scams and Darkweb Activity
Poking around the darknet to create some exercises for a recent OSINT course BLD were delivering, I happened across a scam. Not at all surprising, the darknet is, as Obi-Wan Kenobi might say, “a wretched hive of scum and villainy”. It was of interest to me though, because as a scam involving cryptocurrency I was pretty sure I could figure a few things out if I looked closely enough.
The service was a darknet website advertising snuff. For those who haven’t heard the term, I strongly advise that you don’t even so much as search for it on a clearweb search engine; snuff refers to videos and images of people being tortured and killed. As in, actually tortured and killed for real. That’s right, one of the delights of the darknet is that there are in fact several services offering this content, mostly in return for payment.
The site, pictured below, was offering me access to snuff video in return for a payment of bitcoin. The home screen was plain black with an image of a blood-red doorway and promised “What you see you will not be able to forget”. Before getting access to these ‘unforgettable’ images, I was required to pay bitcoin. 0.00237BTC in fact, which at the time was the equivalent of £110.
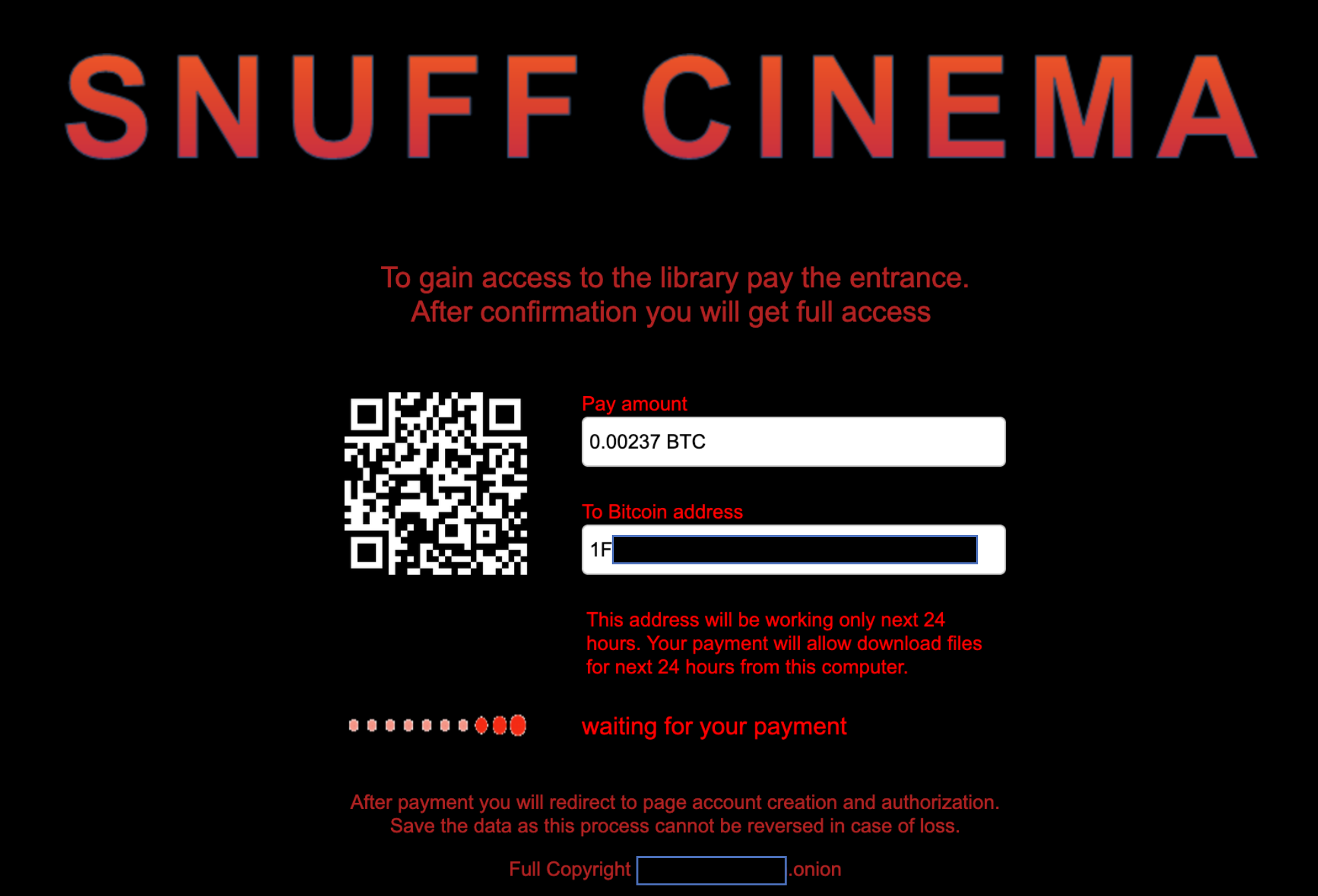
The site provided me with a bitcoin address to which I must pay my funds before it would update and allow me access, and was displaying a small ‘waiting-for-payment’ style animation. It was clear to me that all I had to do was send the bitcoin to the address and the page would then update and I could see all the snuff I could handle.
Armed with even a basic understanding of how bitcoin works, it took me around thirty seconds to conclude that the site was nothing more than a scam, likely consisting of only the one page with a never-ending ‘waiting-for-payment’ animation and nothing more. This is because the pseudonymous nature of bitcoin means that the recipient of a payment will have no immediate way of knowing who has sent the money. To integrate bitcoin as a payment system for an online service, it is normally necessary to provide a new, unused bitcoin address for every instance of the page that is loaded; in other words, a fresh address for each potential customer.
This address is never provided to anybody else, meaning that any incoming payment can be attributed to one particular customer and the service, once paid for, can be provided to the correct person.
The address displayed on my screen, according to the blockchain – a publicly visible ledger of all transactions – wasn’t a new address created just for me. In fact, it had been in use for a couple of years, having received over 450 incoming payments during that time. In other words, had I made my 0.00237BTC/£110 payment, the owners of the address would have no way at all of knowing that it was me making the payment and thus no way of allowing my browser to magically access the horrific material they were advertising.
So, it’s a scam. You might well think ‘Eh, so what? The only people getting scammed are the sickos trying to buy snuff videos, who cares?’ and I wouldn’t disagree with you on that point. What I would draw your attention to though, is those 450 previous payments to the address that I mentioned. On one hand, you could say that they reflect 450 very undesirable people getting defrauded of a few quid. On the other hand, you could say that they reflect lines of enquiry that might identify 450 people who have happily sent significant sums of money to a darknet site trying to sell them videos of victims being butchered for their entertainment.
From a law enforcement point of view, I’d say that’s 450 people who, jurisdiction-depending, ought to be subjects of a detailed intelligence report, if not a firm knock on the door!
There is a misconception that bitcoin is anonymous and untraceable, that those 450 payments can’t be attributed to anybody. In fact, while cryptocurrency absolutely presents challenges, I can tell you that many of those people would be very much identifiable. An investigator armed with the right training and the right tools would quickly identify that a significant chunk of those incoming funds came directly from cryptocurrency exchanges that are compliant with law enforcement requests for information, many with offices in London.
The legality of snuff material is a grey area, however I would point out that these type of scams exist in the form of child abuse imagery, gun sellers, and ‘hitman-for-hire’ services too. The ‘victims’ of these scams would be equally identifiable to investigators with the required knowledge, skills, and tools. Investigations into cryptocurrency thefts, scams and uses within serious crimes is increasing as policing develop a greater understanding of the necessary skills and competencies. Contact us at enquiries@bluelightsdigital.com to find out about our range of cryptocurrency investigation training courses and tools.


